The best
security yet
New features include enhancements to Db2 Mirror, better security configurations and new database features. Hardware updates include that IBM i 7.5 will run on Power10 and Power9 processors and it will fully support up to 48 processors per LPAR on Power10.
Additionally, a new modernisation framework called Merlin has been revealed along with an IBM i subscription option.

Want to speak to an expert?
We’re here to help Get in touch
New features
- SHA2/3 encryption for Password hashing
- Default *PUBLIC Authority on System Supplied Objects
- Check Password Meets Password Rules (QSYCHKPR) API
- Password authentication message and return code changes
- Security by Default
- User centric interface
- High Performing
- Additional metrics for some common functions
- Allows for End to End TLS connection
- Security compliant
The Db2 for i database is the beating heart of the IBM i machine. New database features include Boolean Data, larger indexes and full SQL support.
IBM i 7.5, IBM has bolstered the continuous availability service with several new features which includes a read-only mode and mixed release support.
What is Merlin?
The technologies used to expose IBM i native functions and data promote services-based software – Restful interface connections and enterprise message technologies.
Future versions will contain additional applications based on customer and partner feedback which will be acquired through IBM Certified Container Catalog.
Ready to upgrade?
We can help with implementation and configuration

Protecting your IBM i System
Learn how to improve security with the fundamentals
It has been said that IBM i is one of the most secure operating systems. Unfortunately this is rarely true; not because it isn’t one of the most securable operating systems but because this security doesn’t happen automatically. Someone has to configure it and regularly monitor it and this is where the problem lies. There are many good security products and tools designed to help keep your systems safe, but how good is your security if fundamental areas are overlooked?Intelligent IBM i Security Solutions
Start Your Journey to Better Business
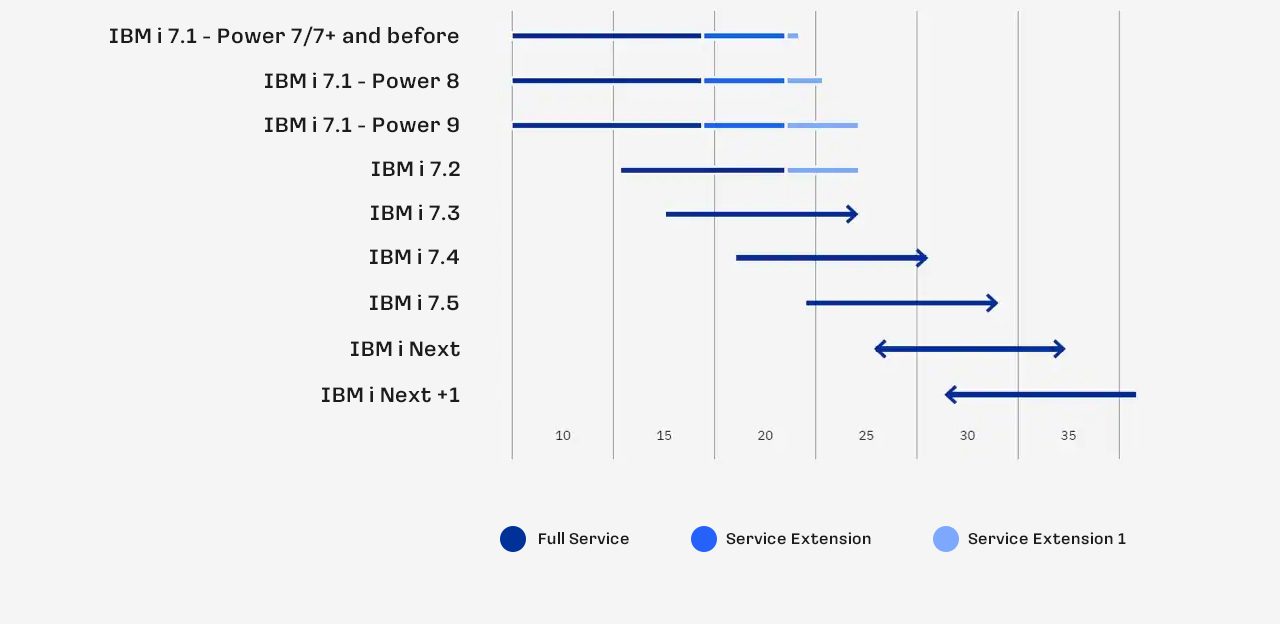
IBM i: Discover the Features
Learn about the benefits of each release from IBM i 7.5 to 7.2
IBM i Roadmap